Linux Telnet
Linux general use as a server, and the server is generally placed in the engine room, in the room you can not operate your Linux server.
This is something we need to telnet to the Linux server to manage and maintain the system.
Linux system via ssh remote login service implementation, the default ssh service port number is 22.
Window System on Linux telnet client has SecureCRT, Putty, SSH Secure Shell, etc. In this paper, Putty example to log into the remote server.
putty Download: http://www.putty.org/
If you downloaded the putty, and then double-click putty.exe following pop-up window.
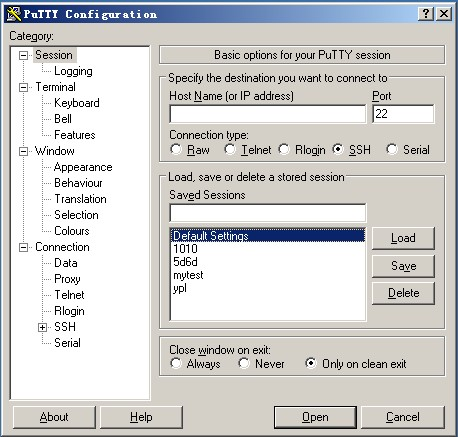
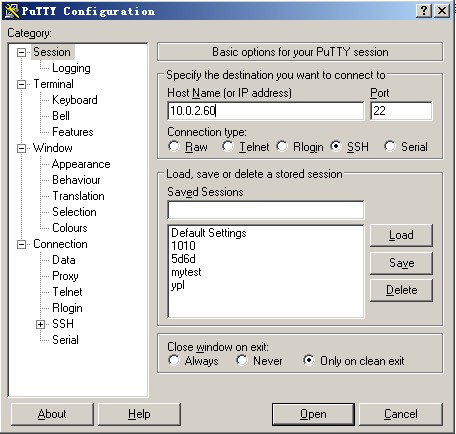
The following input box Host Name (or IP address) you want to log on the remote server IP (ifconfig command can be viewed through server ip), and then press Enter.
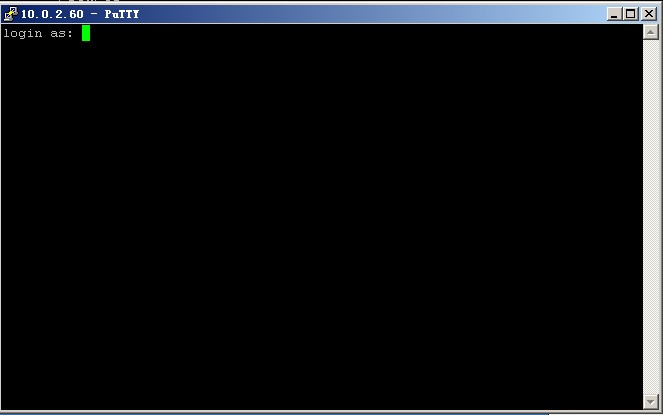
At this time, we are prompted to select the user name.
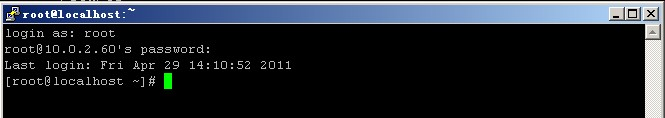
Enter root and press Enter, then enter the password, you can log on to a remote linux system.
Authentication mechanism using the key remote login linux
SSH Secure Shell is the acronym developed by the IETF Network Working Group (Network Working Group).
SSH was established at the application layer and the transport layer on the basis of security protocols.
First, use the tool PUTTYGEN.EXE generate the key pair. Open the tool after PUTTYGEN.EXE shown below:
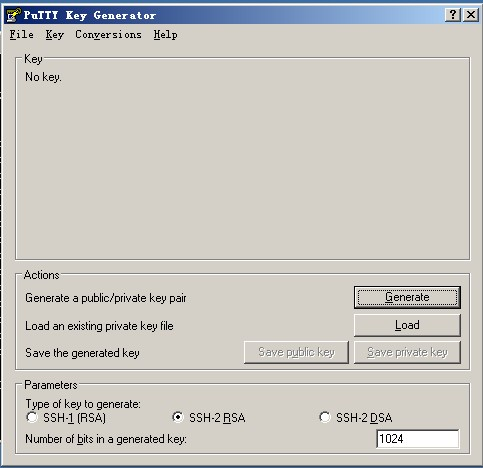
This tool can generate three formats key: SSH-1 (RSA) SSH-2 (RSA) SSH-2 (DSA), we use the default format that is SSH-2 (RSA). Number of bits in a generated key is the size of the generated key, the greater the value, the more complex the generated key, security is higher. Here we write 2048.
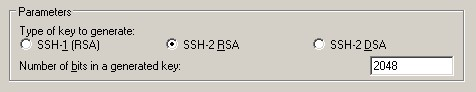
Start and then click Generate to generate a key pair:
Note that, in the process of moving the mouse back and forth, otherwise the progress bar is not moving.
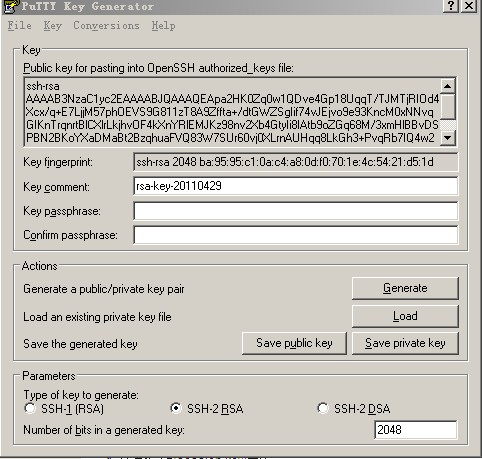
Here, the key pair has been generated. You can give your key to enter a password (in Key Passphrase there) may be left blank. Then Save public key to save the public key and private key points Save private Key saved. I suggest you put a relatively safe place, to prevent others peeping a second to prevent accidental deletion. Next, in relation to the remote linux host set.
1) Create a directory and set permissions /root/.ssh
[Root @ localhost ~] # mkdir /root/.ssh mkdir command to create a directory, it will be detailed later, being only can understand.
[Root @ localhost ~] # chmod 700 /root/.ssh chmod command is used to modify the permissions of the file attributes, it will be described in detail later.
2) Create the file / root / .ssh / authorized_keys
[Root @ localhost ~] # vim /root/.ssh/authorized_keys vim command is a command to edit a text file, as described in detail in subsequent sections.
3) Open the file you just generated public key, it is recommended to use WordPad to open, and looked comfortable, copied from the beginning of the AAAA to "---- END SSH2 PUBLIC KEY ----" everything on the line and paste it into /root/.ssh/authorized_keys file, to ensure that all characters in a row. (You can first copy the contents copied to Notepad, and then edited into a line carrying pasted into the file).
Here to briefly explain how to paste, open that file with vim, the file does not exist, it will automatically create vim. Click on the letter "i" and then press shift + Insert to paste (or click the mouse to the message), provided that has been copied to the clipboard. After pasted, and then move the cursor to the beginning of the line input ssh-ras, and then press the space bar. Press ESC, and then enter the colon wq namely: wq to save. Format as shown below:
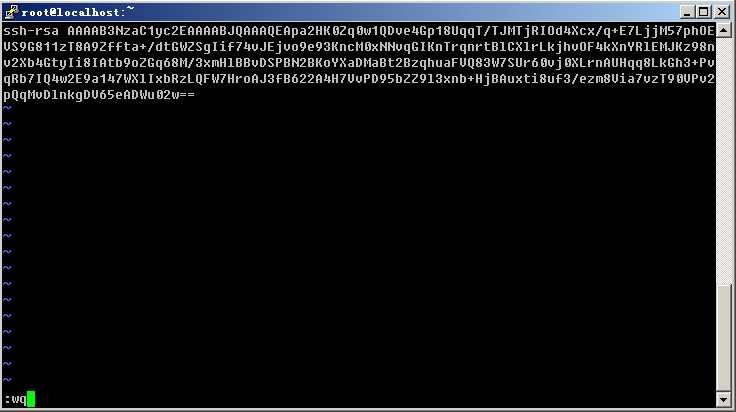
4) then set putty option and click on the left side of the window SSh -> Auth, you click Browse ... to select just the right side of the window to generate a private key, and then point to Open, when the input root, do not type a password to login.
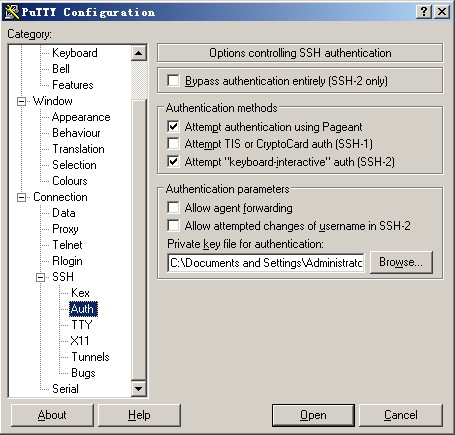
If you set up in front of the Key Passphrase, then the time will prompt you to enter a password. For greater security suggest that you want to set a Key Passphrase.